Zscaler Zero Trust Branch
Zscaler has recently published a new video on their YouTube channel, and I wanted to share a few reflections on what Brian Deitch, Zscaler Chief Technology Evangelist, discussed in his light board presentation.
The video is only 6 minutes long, and it's very much worth watching:
The classic network architecture
Brian starts by highlighting the classic network architecture based on branches, data centers and internet applications, including SaaS and hyperscalers.
Networks are historically segmented using leased lines, VPNs (either telco-provided with MPLS or customer-provided with IPsec site-to-site links) and increasingly SD-WAN, which is still based on site-to-site VPNs but provides a much simpler control plane, in order to centrally manage all the boxes in the branches.
The issue is still there
This classic network architecture is insecure by design, in that it does not implement a minimum discloure of the assets and their entry points, as typically VPNs are created on the internet, and thus an IP address and some TCP or UDP port must be made visible on the firewall, which is often the termination point for said IPsec site-to-site VPNs.
Moreover, there is no specific concept of trust on such connections, and any kind of traffic is allowed from site to site, unless further traffic rules are created and maintained on such network edge devices, adding another layer of complexity to configuration and management of such configurations over time.
Firewall rules, VLANs and NAC are all point solutions which can help, but they only kick the can down the road, and DO NOT solve the security issues that come with such classic network architectures.
What's worse is the fact that while such configuirations happen at the network layer, like ACLs or routing between VLANs, they really are security controls!
Enter the Zero Trust model
Brian then introduces the concept of the Zero Trust Branch "as a cafe", in that there is no trust whatsoever in the network we can find in any cafe or airport lounge, and yet we can make good use of such connectivity by leveraging the advantages of a Zero Trust Exchange like Zscaler's.
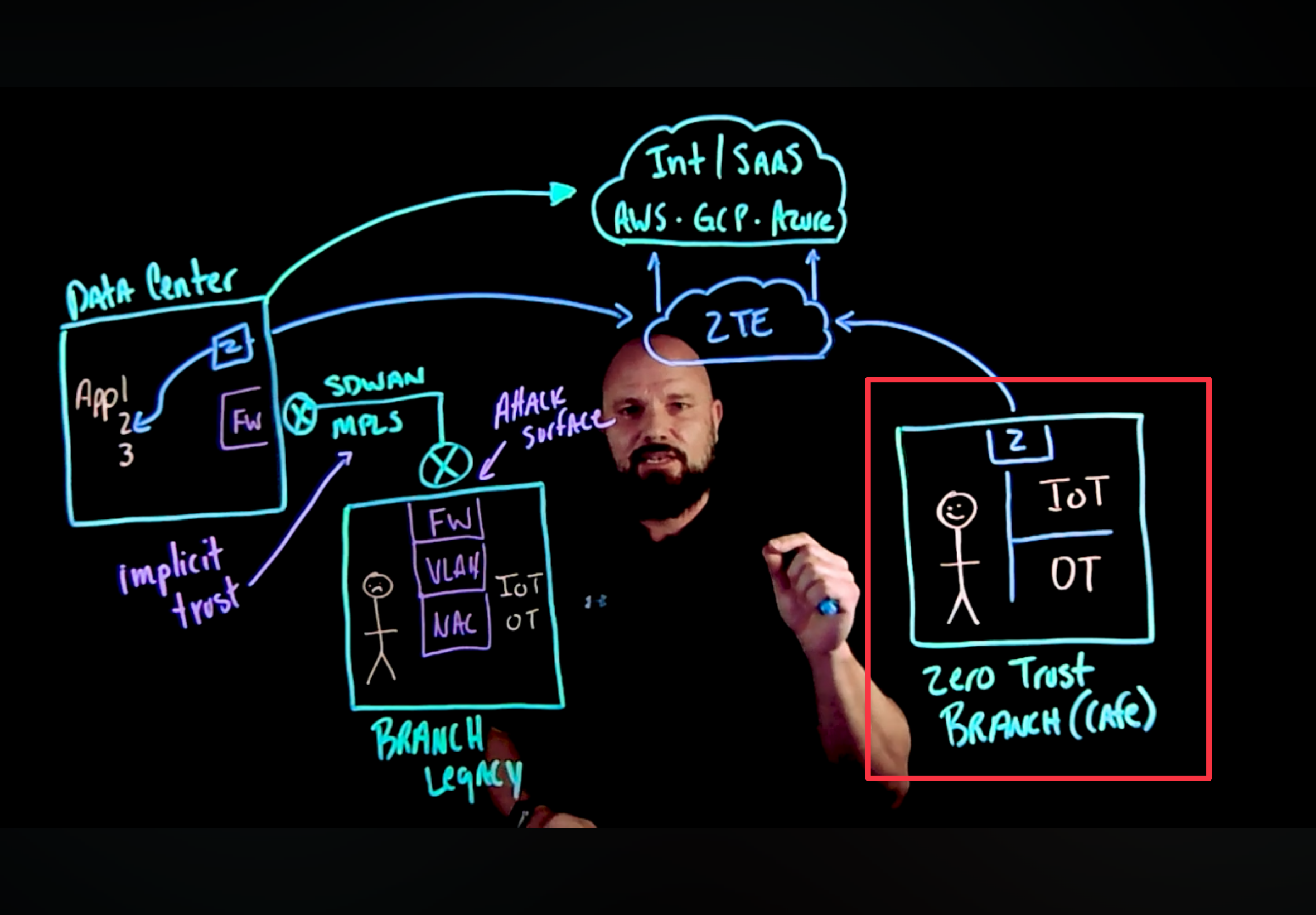
Note the small "Z" in the box at the top center of the Zero Trust Branch as drawn by Brian. That is what's called "Branch Connector" in Zscaler lingo, providing different services for this new kind of branch design.
Brian mentions some key points to this architecture:
- the only thing that's needed in order to activate the connection to the new branch is an internet connection, either a broadband or a cellular connection. Brian does not mention that one also needs to have Zscaler box to perform this function, and it's no wonder that the new Zscaler hardware appliances launched in November 2024 also provide 5G cellular connectivity.

- there is no implicit trust in the network within the branch, its devices and users. It's like a guest network, where all those who need to access every device musty be validated by the Zero Trust Exchange, and will be granted access to the specific applications required.
- by doing this we relegate the network and its appliances to what they really should be doing: pure transport. We don't need to care much at all about the devices configuration, as the router will be "hidden" behind the Edge Appliance, which will also provide DHCP and DNS services, and will correctly proxy traffic to either internal applications (thru what Zscaler calls ZPA) or internet/SaaS applications (thru what Zscaler calls ZIA).
- At NO POINT there will be a network connection, there will only be connections to applications validated by the ZTE. This avoids any issue with lateral movement within the network itself, network which can be made even more secure by further implementing segmentation solutions, which I will cover in a later post.
- this architecture pushes all of the security controls on the ZTE or on the branch edge, in an appliance which is provisioned and managed centrally like any policy, and thus managing the network becomes managing another security policy, done in the same object-oriented policy environment found in ZPA or ZIA.
The last relevant point to make is that the Zscaler Edge Appliance can also host what is called an "App Connector", which can be used by the ZTE in order to allow secure access also to any local server or application in the branch, without any modification to the network. This is particularly relevant in cases such as M&A (mergers and acquisitions), when the IT teams must scramble to somehow "connect" two networks which might have IP addressing overlaps and completely different architectures.
With the correct security policy configured, this kind of connections becomes easy and painless to manage.
Key takeaways
A full and true Zero Trust architecture MUST leverage also the network and the edge, and the approach shown by Zscaler is in my opinion one that is remarkably simple yet provides all the flexibility and security required, while still implementing the classic "trust no one and verify every connection" approach which is the cornerstone of Zero Trust.
I am convinced that this approach will be a remarkable success, and will shape networks of the past in a very different way, starting from today.